Ransomware — it’s not as rare as you think
By Jason Herring and Scott Strasser, June 14 2016 —
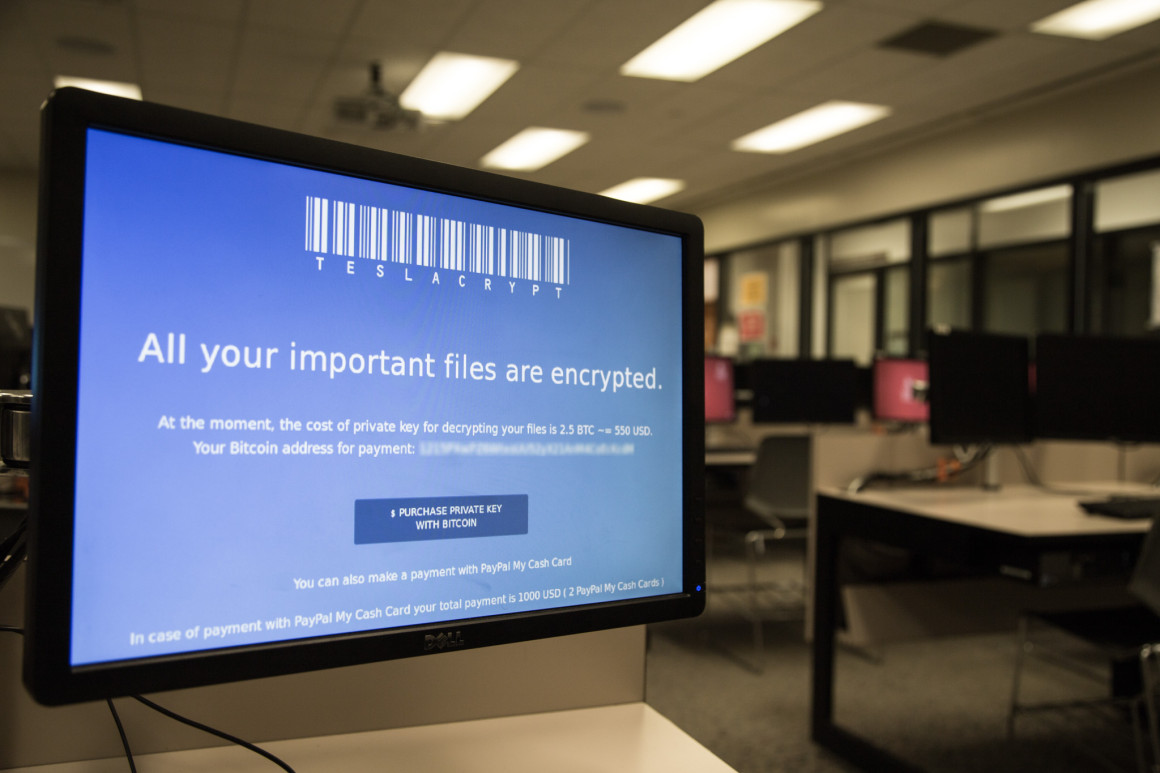
On June 7, the University of Calgary admitted to suffering a ransomware attack — a form of cyberattack that encrypts computer files until a specific sum of money is paid to the attacker.
In order to regain access to the encrypted files, the U of C paid a $20,000 ransom to an unknown source who hacked the university’s computer systems over the May 28–29 weekend. The ransom was paid in bitcoin — an electronic currency that doesn’t leave a paper trail when exchanged on secure networks.
Once the ransom was paid, the attackers supplied the U of C with decryption keys that can be used to restore access to the system.
The malware attack disabled access to the AirUC-Secure wi-fi network, Office 365 webmail, Exchange Email and Skype for Business. It took until June 7 before email issues were fixed. As of June 14, all files are not fully recovered.
The attack coincided with the Congress of the Humanities and Social Sciences, which the U of C was hosting at the time. While the event had its own wi-fi network that was unaffected by the malware, many Congress attendees
noticed the computer issues.
According to U of C computer science professor John Aycock, paying the ransom was a strategic decision by the university.
“Ransomware encryption is at the point where, unless the bad guys made a really serious mistake, you won’t be able to undo it yourself,” Aycock said. “As soon as you look at the whole organization, thinking that everyone in the university loses a couple files, that starts adding up. Some of those files are going to be important, irreplaceable or hard to replace.”
Another factor that motivates paying a ransomware hacker is whether the amount of work required by support staff to fix the problem is more costly than the ransom itself. In cases of post-secondary institutions, Aycock said it’s usually more logical to pay the ransom.
“If you just think of this in terms of the amount of time you have to pay people to recover from this, on the scale of a large institution like the U of C, then the $20,000 the university paid looks like a bargain,” Aycock said.
In a June 7 statement from U of C vice-president finance and services Linda Dalgetty, the university said these kinds of attacks are becoming more prevalent worldwide.
“This attack is part of a disturbing global trend of highly sophisticated and malicious malware attacks against organizations including NASA, law enforcement agencies and large health-care institutions,” the statement read.
Hospitals are an especially common target for ransomware and other data breach attacks, as they rely on up-to-date records of their patients. Losing immediate access to critical files can create problems much larger than having to pay a hacker thousands of dollars. For a hospital, not paying a ransom can put lives at risk.
In February 2016, the Hollywood Presbyterian Medical Centre in California paid $16,900 USD worth of bitcoin when they were hit by a ransomware attack. The centre had lost access to email and digital patient records.
When the story about the U of C broke, many questioned the university’s decision to go public with their willingness to pay the ransom, stating it makes the university appear vulnerable to future attacks. According to Aycock, ransomware attacks often go unreported due to fears of bad publicity.
“When you’re reading about these things, you’re reading about them from institutions who have confessed to paying the ransom,” Aycock said. “In all likelihood there are many more who have been hit by it and paid the ransom and don’t make it public or perhaps are afraid to because they think it might do damage to their reputation.”
Despite paying the $20,000 ransom, services still aren’t fully restored at the U of C. IT had to recreate over 9,000 new Office 365 email accounts for U of C staff due to the attack. IT is still working to evaluate the attacker’s decryption keys and save as many files as possible.
Ultimately, Aycock hopes the attack teaches a valuable lesson in data security for other institutions across the country.
“The university is acting in one of its key roles — the university is supposed to be about teaching and research and it’s teaching a valuable lesson to the community,” Aycock said. “It didn’t come at zero cost, but I think it’s a valuable lesson if people say, ‘hey, I’ve got to shore up my backups and take action against this.’ That could save a lot of people money down the line.”
Due to the attack’s criminal nature, the Calgary Police Services are now involved with the investigation. As the investigation is ongoing, neither the university nor the CPS will comment on the case’s specifics.
